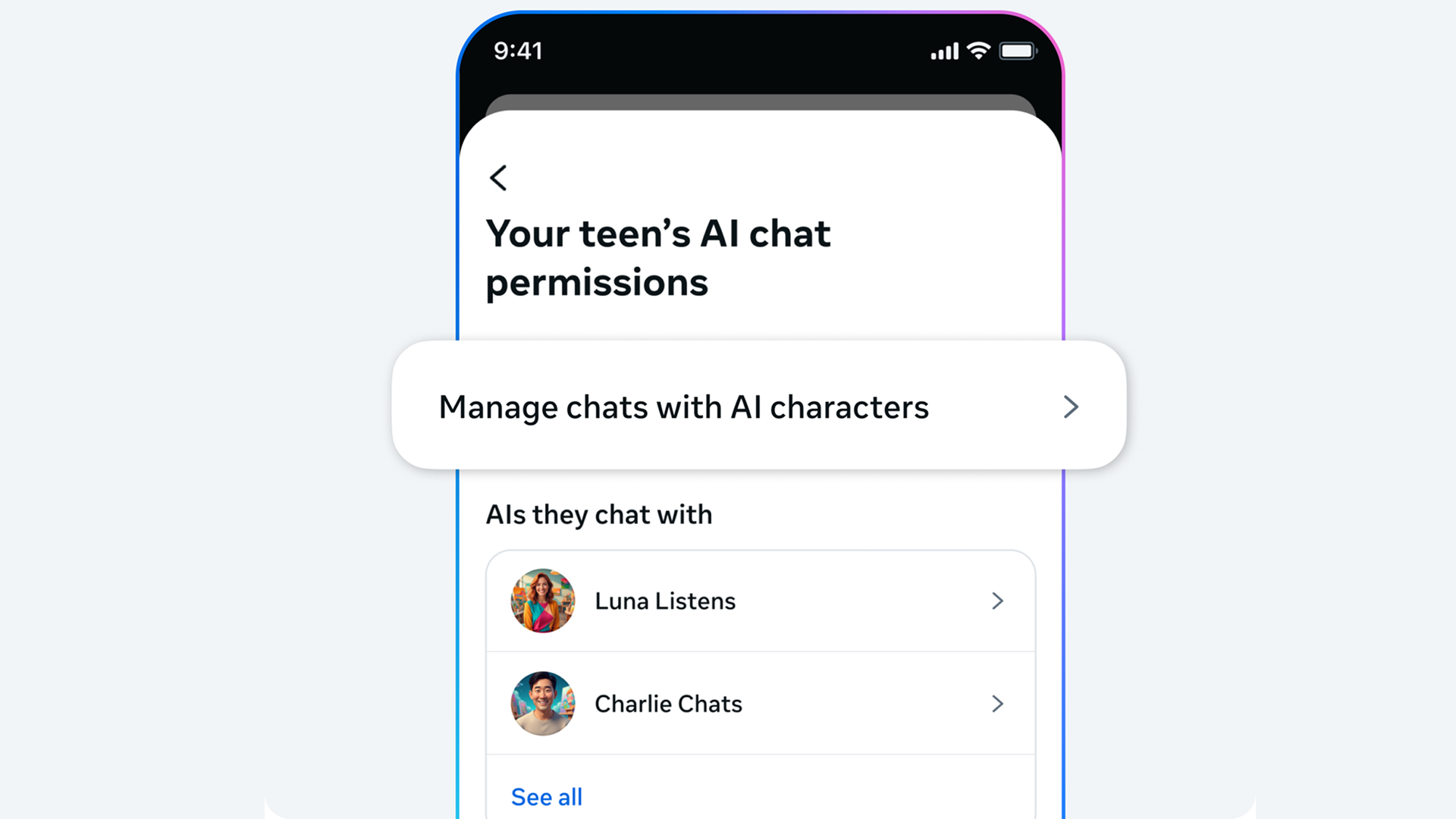
Meta plans to roll out new parental controls around teens' access to AI character chats on InstagramParents will also get...
Insider Brief Chinese researchers claim to have begun mass-producing a single-photon detector, a core component for quantum radar systems that...
Fujitsu A77-K3 has an optical drive and Intel Core processorThe A77-K3’s large display and solid build target long-hour productivity usersFujitsu...
Now the Windows 10 end of life deadline has passed, you may be looking to upgrade your work device to...
Halloween is nearly here, and as the nights get darker, what better way to celebrate than with a good ol’...
Editor's note: We're also running live hubs today with even more recommendations:US: Prime Day ends today – we've picked the...
There are moments in defence history when a single leak does more damage than a thousand missiles. The Black Mirror...
Two factors often determine stock prices in the long run: earnings and interest rates. Investors can't control the latter, but...
IBM says its IDE early adopters have seen a 45% boost in productivityClause is the LLM of choice for AI...
The whole tech world might be enamoured with the iPhone 17 range right now (including the ever-so-svelte iPhone Air), but...